IN last article I told you what tricks you can do with just a browser. We will need this knowledge further
Hot August 2020 showed that basic measures are too few and ineffective. Need something more
When choosing a solution, I set myself several goals:
The solution must be open
The solution must be free - this is the only way it can become widespread
The solution must be decentralized - there should be no single point of failure
Homeless VPN. I wanted to be able to connect to any network node for free
Bum hosting. Corollary of the previous point. Possibility to roll out a test resource for free
The VPN fell off immediately: even the working VPN died. VPN requires a centralized external server - a single point of failure. Finally, the VPN is paid - I wouldn’t call myself a rogue personally, but it’s definitely not a mass option
I haven't considered TOR yet. This is a completely viable solution, but I lack the expertise. In the comments, I call for an explanatory team about the strengths and weaknesses of the actual operation of TOR. Comparison of I2P and TOR networks
I started learning I2P. The idea seemed nice to me. It is especially interesting that the network will not only withstand a sharp increase in the number of users, but this will only make it work more reliably (but this is not certain). On the lurka very inspiring description of the possibilities, and wiki brings down from heaven to earth and makes it clear that I2P is not a silver bullet, and de-anonymization attacks are a reality. Difficult and expensive, but possible. For comparison, without I2P it’s like using your passport to introduce yourself and prepare for a search
Opportunities, limitations and pain points
Just like the TOR network, the I2P network has exit nodes. This means that you can access the regular Internet through the I2P network. However, you should understand that the speed of operation leaves much to be desired - streaming video via I2P is a so-so idea
Interestingly, you can reach TOR nodes from the I2P network. We will definitely set this up
I2P does not limit itself to any protocol. Instead, the network provides a medium for transmitting data. I was forwarding a connection to the database over an I2P network. I2P tunnels allow you to forward any resource, thus making it available for use by any program. If someone is not familiar with tunnels, the idea is simple and consists in opening a port on your machine for some open port on a remote server, and then using any local program to connect to the local port, which is exactly what any program can do, and the intricacies of transfer bytes to that port of the remote machine and back are already handled by the tunneling program (special case of a tunnel).
The consequences of tunnels are bum VPN and bum hosting. I'm happy - I can roll out the resource for free. I can connect 2 machines for free. Any other network member can do the same for free. Tasty
The network will be able to function even if playful hands again reach for the Big Switch - the Belarusian realities are exactly like this, he exists
The sore point is changing routes (hence dest hash). But I hope that the problem can be solved - there is a version for Android, which involves switching between the operator’s network and different wifi access points, and an experimental “Laptop Mode” has appeared in the router settings»
Errors and misconceptions
I've noticed several patterns of misconceptions
Oh, they told me on TV that they show this on your i2p! Is this actually legal??
Believe rumors more. There is nothing there that is not on the regular Internet. I2P aims to be a data transmission medium. The TCP and UDP protocols transmit more than 99% of information on the Internet, including illegal content. Let's fight the content, not the transport of its delivery
When the Internet is turned off, I’ll definitely install it
And you will cuckoo until the network is restored. I2P is not magic to bypass censorship, but a very real overlay network of flesh and blood, which receives information about other network participants only during its work
Okay, I installed it, launched it, poked something, and turned it off. As soon as the Internet is turned off - wow, seven of me! I’ll turn on I2P and everything will be wonderful for me!
Same problem. With a high probability, you will not be able to find any of those with whom you previously established a connection. Run I2P as a service and let it hang in the background. She doesn't ask for food (well, except for memory). This is the only way you will meet the hour in readiness
I'll be a minute. There and back
Nodes that often break connections with other network participants, according to established tradition get in the jug end up on ban lists. This rule should not be taken as an absolute; it is simply desirable that the service runs in the background. Don't jerk her every time she sneezes - she doesn't bite and doesn't ask to eat.
Well, a completely kosher stop of the I2P service is to press the “Shutdown” / “Turn off” button in the router console. The I2P daemon will stop itself in the worst case after 10 minutes - as soon as the already established connections with other participants in the i2p network expire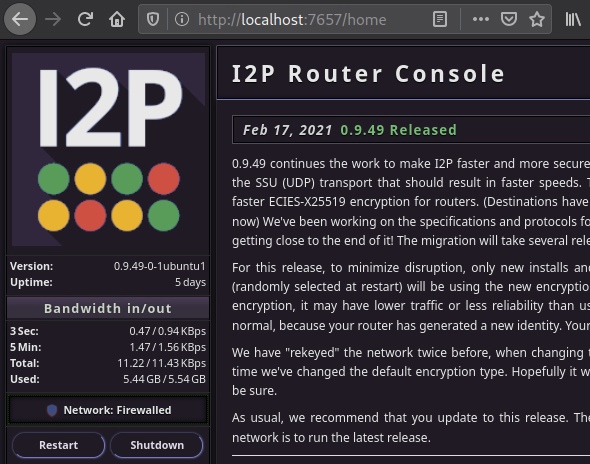
Installation on desktop
It consists of two mandatory parts - installing a gateway (inproxy) and setting up a browser (light or hard - we choose it to your taste). It is important to complete both stages; they do not make sense separately.
Gateway installation
on official project website there is a list of downloads - you can take it from there
The same list contains a section «Packages for Debian/Ubuntu»
After installation we try to open http://localhost:7657/ — router web console. I highly recommend bookmarking the page or even Pin Tab. If the page opens, you did everything right
Browser settings. Light
In this case, we are making the assumption that you are doing nothing wrong and are simply seeking access to information that has upset your government. And the government, like a whiny little girl, tends to be offended by any information. For example, linkedin is blocked in Russia. A terribly dangerous and extremist resource, yeah
In this case, we are not afraid of information leaks. For example, a site on the i2p network may request some jquery from a CDN. What is it about a js library that is requested millions, if not billions of times a day??
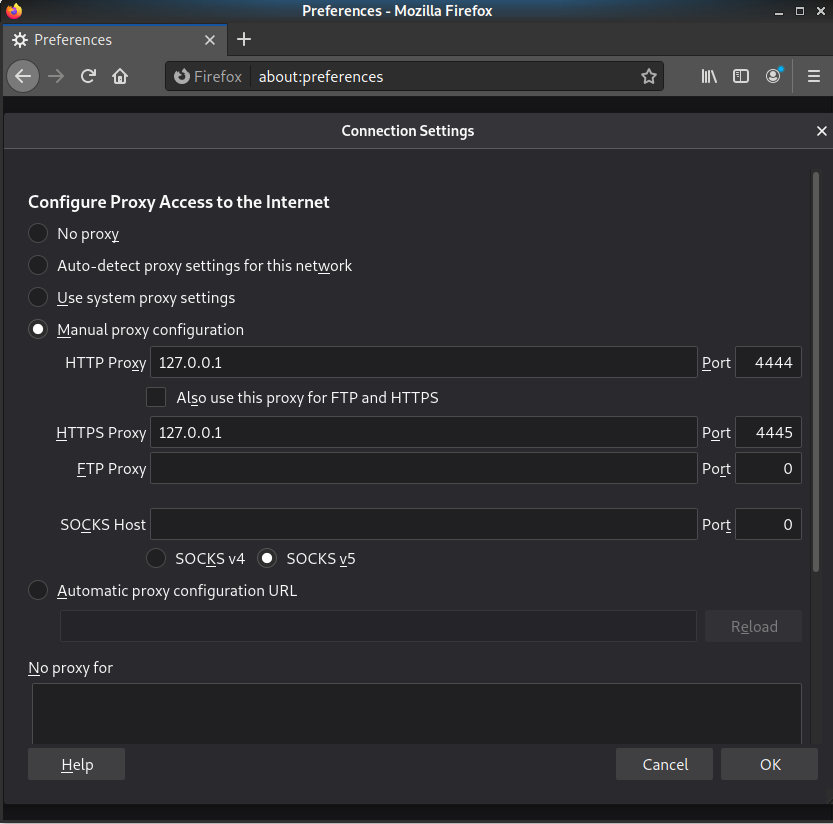
To configure we need an add-on SmartProxy. Setup is done in 2 simple steps - you need to add the I2P input gateway to the list of proxy servers and create proxy rules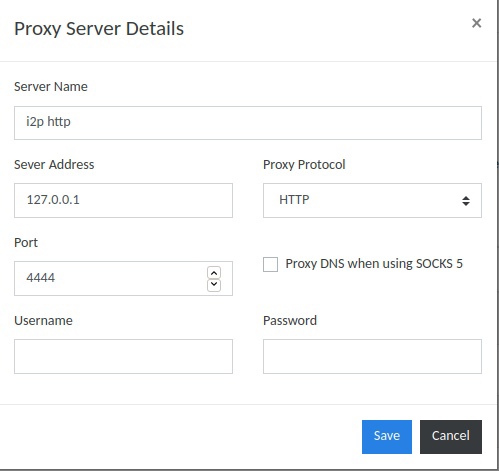
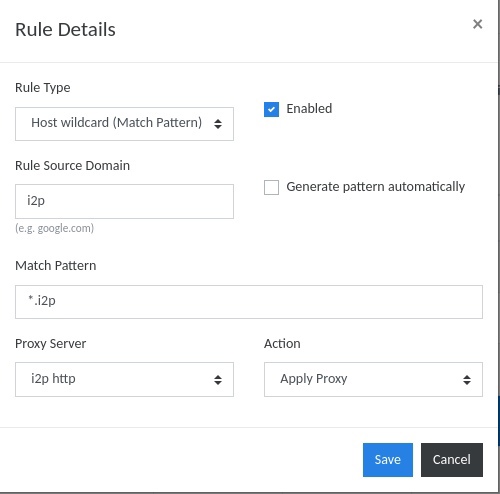
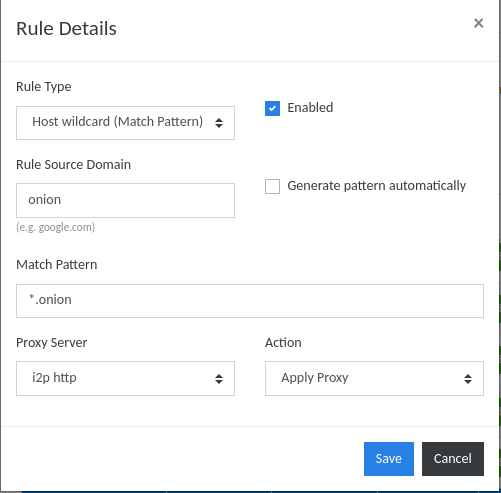
Browser settings. For those who like it harder
Paranoia may require guarantees that there will be no leaks. It does not follow from the presence of paranoia that we will rush to look at the previously mentioned website of Comrade Major Vasily Musorov. Setup is carried out in a few simple steps
I don't have an extra browser on my system to dedicate it entirely to I2P. I will use the already installed firefox. The following option works on Linux:
FIREFOX_PROFILE="firefox-i2p"
FIREFOX_HOME="${HOME}/${FIREFOX_PROFILE}"
mkdir -p "$FIREFOX_HOME"
env HOME="$FIREFOX_HOME" firefoxThat is, the idea is simple: make Firefox work with a completely clean profile, which will not affect the main one in any way, and which we can demolish at the first hint of problems, like a grandfather’s testicle. No matter what additions we install there, no matter what settings we make there, you can continue to use the main profile
I don't have a single Windows or MacOS machine. In the comments, please tell us how to do a similar trick with your ears in Windows. And on MacOS this trick should work, but I haven’t tested it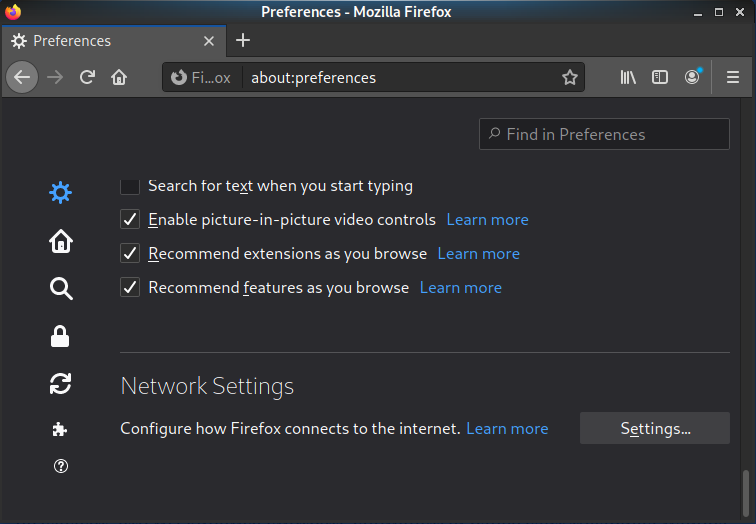
Installation on Android
The essence is exactly the same, but the tools are slightly different
Gateway installation
Still the same downloads page there is a section “Android»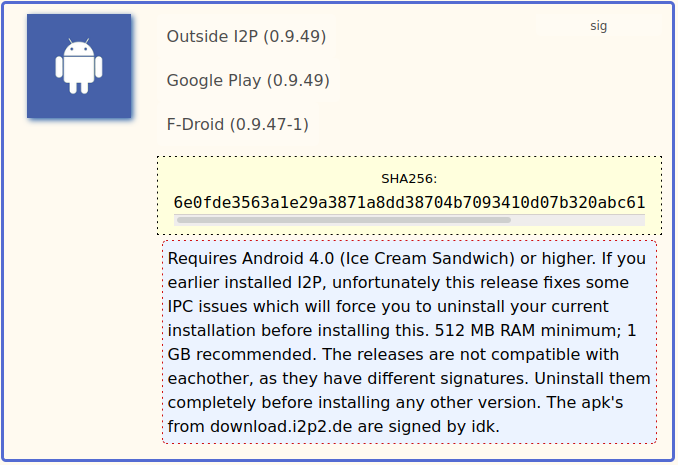
Browser settings. Light
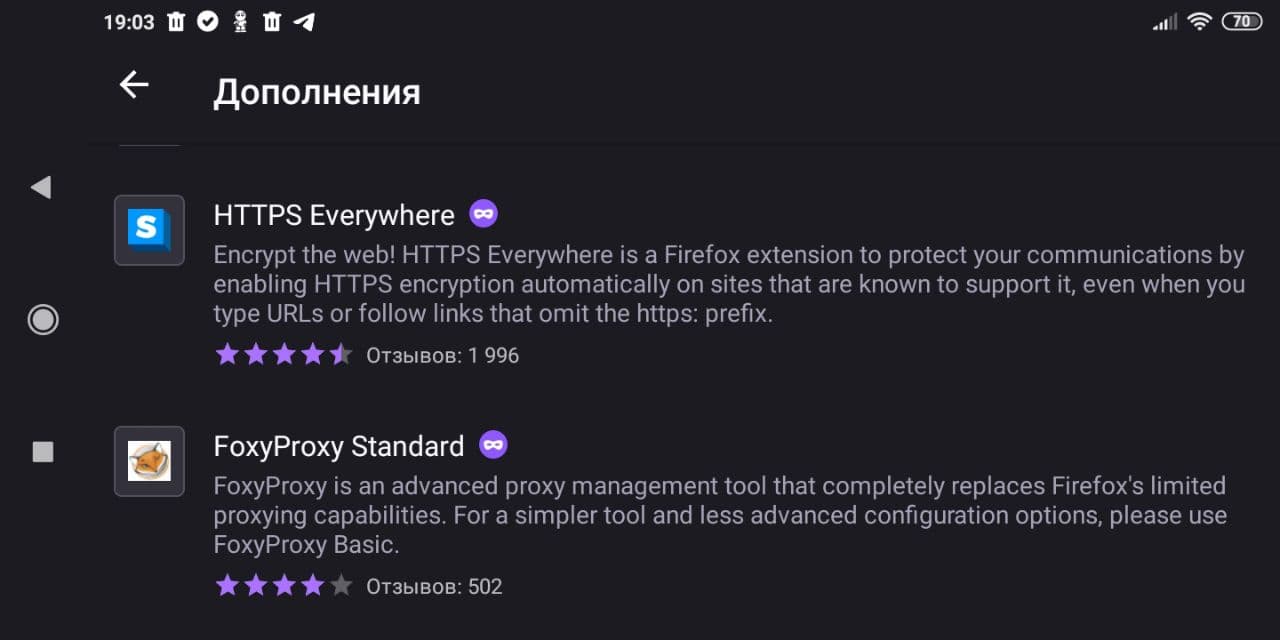
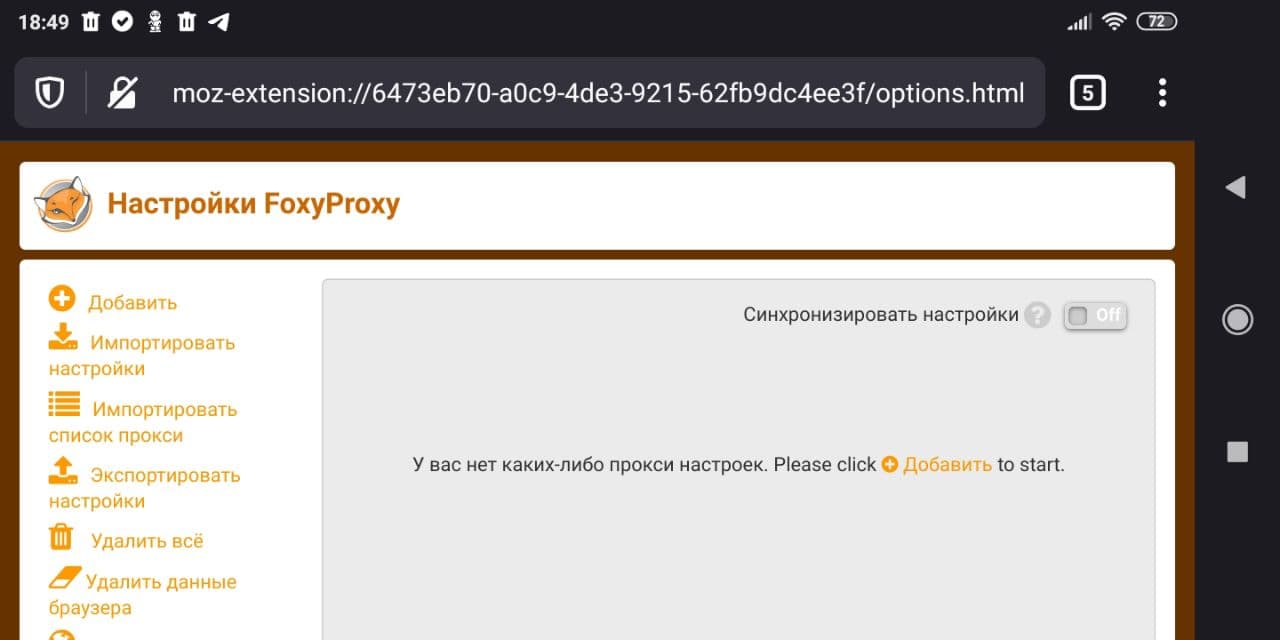
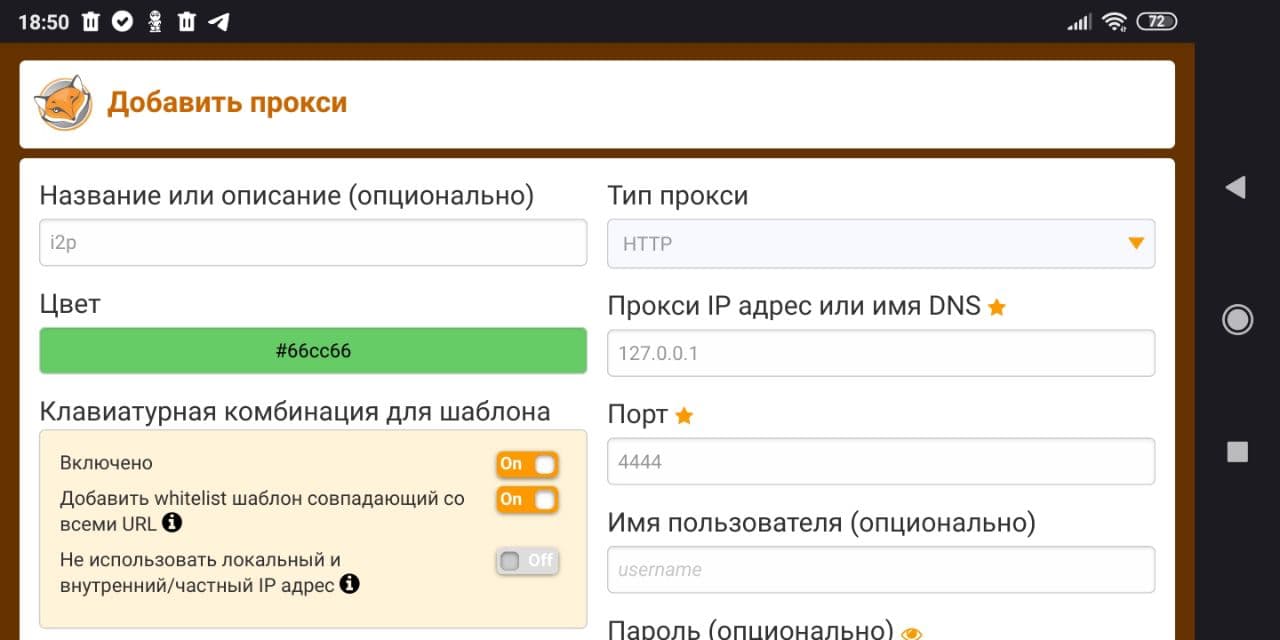
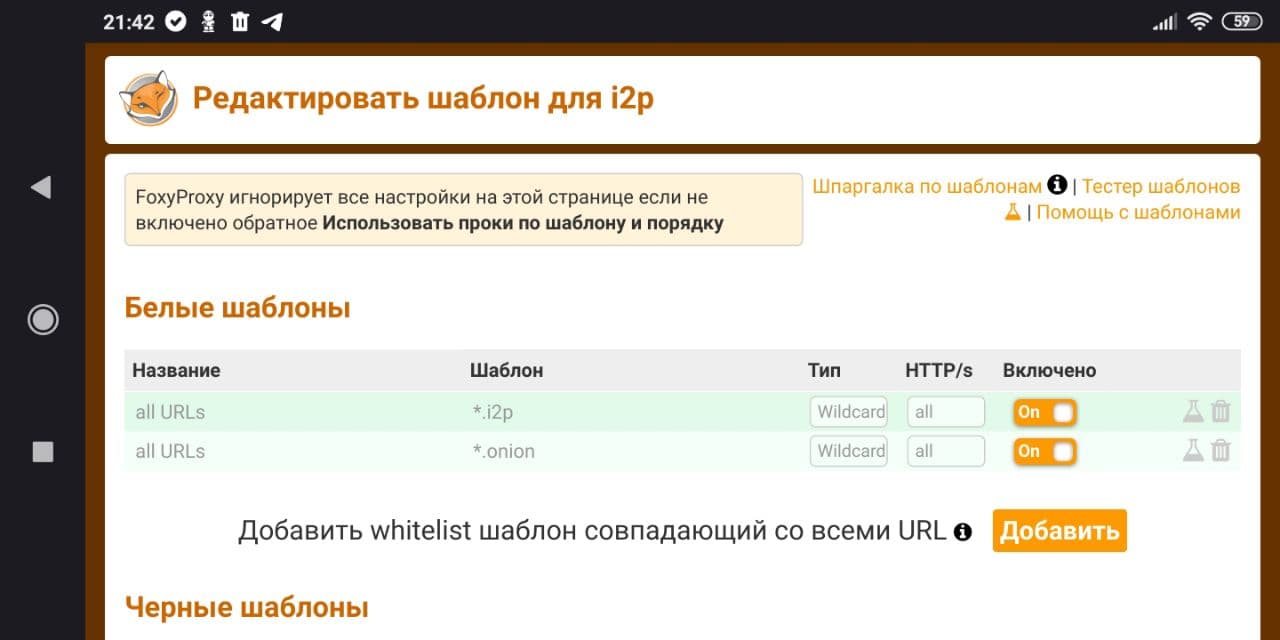
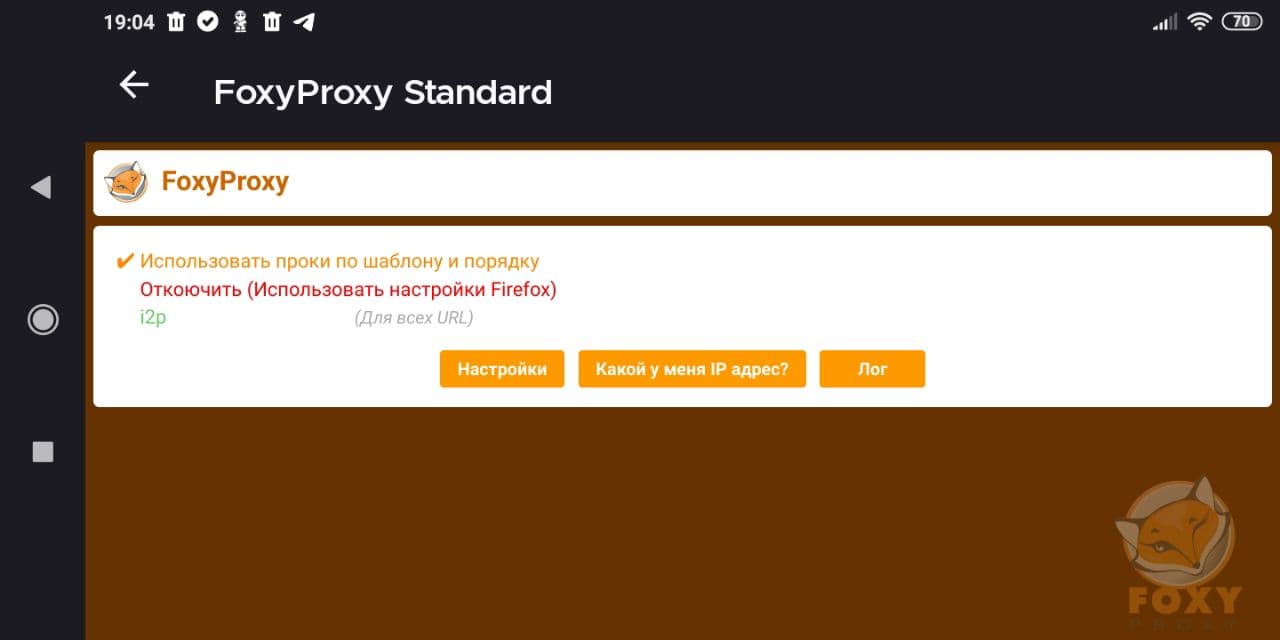
Recipes for setting up
I'll tell you about a few optional steps
DNS-over-HTTPS
For those who haven't read it previous article: needs to be added I2P And onion to exceptions. Otherwise, the browser will try to resolve these domains on Cloudflare with predictable results
I2P + uBlock Origin
We know how to learn from mistakes, therefore, we will add the i2p and onion zones to the exceptions, thus completely disabling the ad blocker for all i2p and onion resources
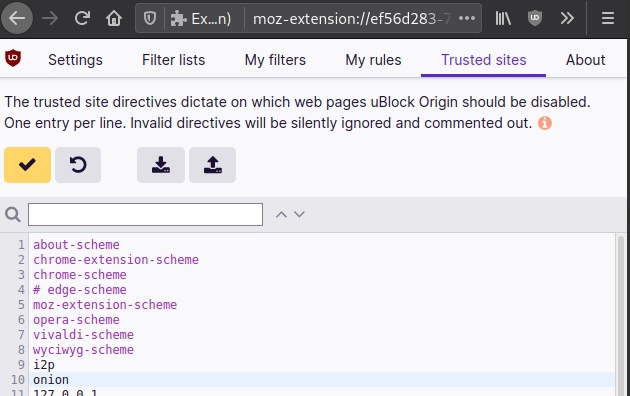
It’s better than it was, but not perfect—you lose control over downloading third-party content. I would just like to disable the resolution of i2p and onion names
Additional subscriptions
IN subscription list it makes sense to add addresses:
http://stats.i2p/cgi-bin/newhosts.txt
http://identiguy.i2p/hosts.txt
http://isitup.i2p/alive-hosts.txt
http://reg.i2p/export/hosts.txt
http://inr.i2p/export/alive-hosts.txt
Feed java memory
The I2P ingress gateway is written in java. By default it starts with a limit of 128M. This is enough to get acquainted and slowly immerse yourself in the brave new world of the invisible Internet. The component that consumes the most memory is NetDB, a database of other hosts on the I2P network. The more of them are known, the higher the reliability and the higher the likelihood that at hour H, when the Internet dies again, you will still be able to find a loophole - an accessible host from the list of known ones. True, there are no guarantees
In case of Ubuntu/Debian:
sudo dpkg-reconfigure i2pI don’t know how to do this for Windows and I really hope for comments
When you can’t open a port less than 1024, but you really want to, then you can
A very controversial recipe. In general, there is no need to do this. But if you really want to, then you can. I did this to test out the capabilities of I2P. That is, just for fun
The adventures began with the question “so where is java?”?»
which java | xargs file --mime-type
/usr/bin/java: inode/symlinkOK
which java | xargs readlink | xargs file --mime-type
/etc/alternatives/java: inode/symlinkMore symlinks for the symlink god!
which java | xargs readlink | xargs readlink | xargs file --mime-type
/usr/lib/jvm/java-11-openjdk-amd64/bin/java: application/x-pie-executablePlease understand that my configuration may not be the same as yours. The idea is simple - add a section in the middle xargs readlink until enlightenment occurs - for now file won't tell application/x-pie-executable. As soon as java is found, we remove the last 2 words from the resulting command file --mime-type, for example, by pressing ^W twice, and add instead setcap 'cap_net_bind_service=+ep':
which java | xargs readlink | xargs readlink | xargs setcap 'cap_net_bind_service=+ep'You may also need to add the ability to open a raw socket setcap 'cap_net_raw=+ep':
which java | xargs readlink | xargs readlink | xargs setcap 'cap_net_raw=+ep'But next time I'll just deploy docker with nginx
What else is there??
I highly recommend reading it Russian-language wiki and look through the lists identiguy or isitup. And there is also search engine
And there is also Telegram MTProto proxies. The idea comes down to creating tunnels to the specified i2p hosts. Instructions on the website
There are also torrents and mail. I haven't tried any of this yet
Found filibuster And ebooks.i2p — the latter looks generally expensive and rich
Instead of a conclusion
It should be understood that I2P is not an independent resource, but primarily a feeder - a data transmission medium. Therefore, the scope of applicability of the technology is quite wide and rests, rather, on the imagination
I didn't say a word about i2pd. The project is worthy of attention: it is more productive with less resource consumption. I don't have any expertise yet